Log Collection Ability
When you perform log management, you cannot save or analyze logs as trails unless you have the necessary logs.
MylogStar acquires logs at the kernel level of the OS. This enables you to grasp the operations whose logs cannot be acquired by other log management products.
The acquired logs are highly accurate and can be utilized for information leakage prevention and work improvement.
Log acquisition at the OS kernel level
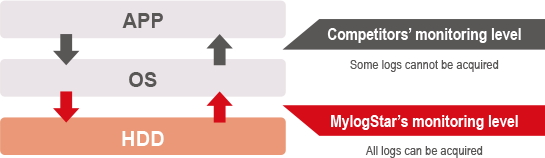
MylogStar acquires file operation logs at the kernel level of the OS.
This allows it to acquire logs for all file operations performed in accordance with the file system, regardless
of whether they are initiated via the GUI or CUI (command prompt). MylogStar can log the behavior
of the OS accurately without relying on any application or environment.
 Acquire information about 15 types of client operations
Acquire information about 15 types of client operations
MylogStar can acquire all the logs needed for trail management, including those of login, logoff, and file operations.
For e-mails and web access, MylogStar monitors communication packets, which allows you to see what is done over the network.
MylogStar collects all the necessary logs.That is the first step in log management.
|
Computer logs The powering on and off of a computer (“power on”, “power off”, “suspended”, and “recovery from suspension”) are recorded. |
E-mail logs The subject, mail source and destination addresses (FROM, TO, CC, and BCC), transmission and reception times, mail body, file attachments, mail size, file attachment names, and number of file attachments are recorded. |
Clipboard logs The name of the application used for each copy operation and the contents of the clipboard (character strings and file paths) are recorded. |
|||
|
User logs The login and logoff, actual operation time, and remote connection source IP address and host are recorded. |
Web logs The URL, page title, host name, acquisition time, and action (GET or POST) are recorded. SSL and TLS are supported. |
TCP session logs Specified ports are monitored. When a TCP session is established, the source and destination IP addresses and the communication port are recorded. |
|||
|
Application logs The product name, version, start time, end time,active time, and application name are recorded. |
FTP logs The destination address, destination port,source address, source port, FTP command,FTP command data, etc. are recorded. |
Event logs Windows event logs are acquired. Login failures, folder access failures, changes to the server OS settings, etc. can be recorded. |
|||
|
File logs Files operations, such as creating new files in the local drive, network drive, removable drive,etc. and copying, renaming, and deleting existing files, are recorded. The logs of operations performed at the command prompt can also be acquired. The attachment and detachment of external devices are recorded. The file sizes are acquired. |
Window logs The title of the active window is recorded. The start and end times, as well as the active time,can be acquired. |
Web mail logs Gmail and Office 365 are supported. The subject, transmission time, TO, CC, BCC, mail body, etc. are recorded. |
|||
|
Printer logs The document name, printer name, acquisition time, number of pages, application name,printed file path, etc. are recorded. |
Screenshot logs Screen images are recorded according to flexibly set conditions, such as at regular intervals (60 seconds to 8 hours), when the Print key is pressed, when a specific website is viewed, and when a file is uploaded. |
Inventory logs The information about the computer hardware and software is recorded. |
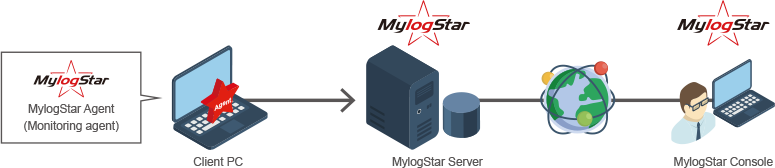
Image of the MylogStar configuration